Parent class: VirWare
Viruses and worms are malicious programs that self-replicate on computers or via computer networks without the user being aware; each subsequent copy of such malicious programs is also able to self-replicate. Malicious programs which spread via networks or infect remote machines when commanded to do so by the “owner” (e.g. Backdoors) or programs that create multiple copies that are unable to self-replicate are not part of the Viruses and Worms subclass. The main characteristic used to determine whether or not a program is classified as a separate behaviour within the Viruses and Worms subclass is how the program propagates (i.e. how the malicious program spreads copies of itself via local or network resources.) Most known worms are spread as files sent as email attachments, via a link to a web or FTP resource, via a link sent in an ICQ or IRC message, via P2P file sharing networks etc. Some worms spread as network packets; these directly penetrate the computer memory, and the worm code is then activated. Worms use the following techniques to penetrate remote computers and launch copies of themselves: social engineering (for example, an email message suggesting the user opens an attached file), exploiting network configuration errors (such as copying to a fully accessible disk), and exploiting loopholes in operating system and application security. Viruses can be divided in accordance with the method used to infect a computer:- file viruses
- boot sector viruses
- macro viruses
- script viruses
Class: Net-Worm
Net-Worms propagate via computer networks. The distinguishing feature of this type of worm is that it does not require user action in order to spread. This type of worm usually searches for critical vulnerabilities in software running on networked computers. In order to infect the computers on the network, the worm sends a specially crafted network packet (called an exploit) and as a result the worm code (or part of the worm code) penetrates the victim computer and activates. Sometimes the network packet only contains the part of the worm code which will download and run a file containing the main worm module. Some network worms use several exploits simultaneously to spread, thus increasing the speed at which they find victims.Read more
Platform: Linux
Linux is a family of UNIX-influenced operating systems based on the Linux kernel and GNU tools.Description
Technical Details
This is the first known worm infecting RedHat Linux systems. The worm was discovered in the middle of January 2001. The worm spreads itself from system to system by using a RedHat security breach (a so-called "buffer overrun" breach) that allows for uploading to a remote system and running a short piece of code there that then downloads and activates the main worm component.
The worm has not been tested in VirusLab, so all information below should be read as "the worm could do, if it really does work." We also have no confirmed reports about infected servers from our customers.
The worm uses three security breaches in RedHat versions 6.2 and 7.0, these breaches were discovered in summer-autumn 2000, at least three monthes before the worm was discovered.
The worm also contains routines that intend to attack FreeBSD and SuSE machines, but these routines are neither activated, nor used in worm code.
The Worm Itself
This is a multi-component worm that consists of 26 files about 300K in total length. These files are script programs and executable files. The script programs are ".sh" files that are run by a Linux command shell (like DOS BAT files and Windows CMD files). The executable files are standard Linux ELF executables.
The main components of the worm are script ".sh" files that are run as hosts, and then run the rest of the files (additional ".sh" files and ELF executables) to perform necessary actions.
The list of components appears as follows:
asp hackl.sh randb62 start62.sh wh.sh asp62 hackw.sh randb7 start7.sh wu62 asp7 index.html s62 synscan62 bd62.sh l62 s7 synscan7 bd7.sh l7 scan.sh w62 getip.sh lh.sh start.sh w7
The "62" components are activated under RedHat 6.2 systems, the "7" components are activated under RedHat 7.0. The "wu62" file is not used at all.
Spreading
Spreading (infecting a remote Linux machine) is done by a "buffer overrun" attack. This attack is performed as a special packet that is sent to a machine being attacked. The packet has a block of specially prepared data. That block of packet data is then executed as a code on that machine. This code opens a connection to an infected machine, obtains the rest of the worm's code, and activates it. At this moment, the machine is infected, and starts to spread the worm further.
The worm is transferred from machine-to-machine as a "tgz" archive (standard UNIX archive) with a "ramen.tgz" name, with 26 worm components inside. While infecting a new machine, the worm unpacks the package there, and runs the main "start.sh" file that then activates other worm components.
The worm components then scan the global network for other Linux machines and upload the worm there if the "buffer overrun" attack is performed successfully.
The worm also appends a command to run its starting ".sh" file to a "/etc/rc.d/rc.sysinit" file, and as a result, the worm's components are activated upon each followed system start.
The worm also closes security breaches that have been used to infect the system. So, an infected machine cannot be attacked by the worm twice.
Details
To obtain IP addresses of remote machines in order to attack them, the worm scans the available global network for IP addresses; i.e., operates similar to standard "sniffer" utilities.
To attack a remote system, the worm uses security vulnerabilities in three RedHat Linux demons: "statd", "lpd", and "wu-ftp".
To upload and activate its copy on a remote machine, the worm "buffer overrun" code contains instructions that switch to "root" privileges, runs a command shell, and follows the ensuing commands:
- creates a directory to download the worm "tgz" file, the directory name is "/usr/src/.poop"
- exports a "TERM=vt100" variable that is necessary for the next step
- runs "lynx" (simply WWW browser) that downloads a worm "tgz" file from a host machine (the machine from which the worm is spreading)
- unpacks all worm components from a "tgz" archive
- runs the worm startup component: the "start.sh" file
To send a "ramen.tgz" archive, the worm runs an additional server "asp" that sends the worm's "tgz" archive by request from a worm "buffer overrun" component.
Misc.
The worm has several payload and other non-infectious routines.
First of all, it finds all "index.html" files (a Web server's starting pages) on a local machine starting from the root directory and replaces them with its own "index.html" file that contains the following text:
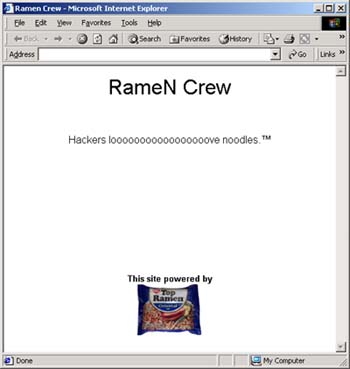
The worm deletes the "/etc/hosts.deny" file. This file contains a list of hosts (addresses and/or Internet names) that are denied access to this system (in case a so-called TCP wrapper is used). As a result, any of the restricted machines can access an affected system.
When a new system is infected, the worm sends "notification" messages to three e-mail addresses:
- the address of just the infected machine
- gb31337@hotmail.com
- gb31337@yahoo.com
The message Subject is IP address of infected machine, the message body contains the text:
Eat Your Ramen!
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com