Parent class: VirWare
Viruses and worms are malicious programs that self-replicate on computers or via computer networks without the user being aware; each subsequent copy of such malicious programs is also able to self-replicate. Malicious programs which spread via networks or infect remote machines when commanded to do so by the “owner” (e.g. Backdoors) or programs that create multiple copies that are unable to self-replicate are not part of the Viruses and Worms subclass. The main characteristic used to determine whether or not a program is classified as a separate behaviour within the Viruses and Worms subclass is how the program propagates (i.e. how the malicious program spreads copies of itself via local or network resources.) Most known worms are spread as files sent as email attachments, via a link to a web or FTP resource, via a link sent in an ICQ or IRC message, via P2P file sharing networks etc. Some worms spread as network packets; these directly penetrate the computer memory, and the worm code is then activated. Worms use the following techniques to penetrate remote computers and launch copies of themselves: social engineering (for example, an email message suggesting the user opens an attached file), exploiting network configuration errors (such as copying to a fully accessible disk), and exploiting loopholes in operating system and application security. Viruses can be divided in accordance with the method used to infect a computer:- file viruses
- boot sector viruses
- macro viruses
- script viruses
Class: Email-Worm
Email-Worms spread via email. The worm sends a copy of itself as an attachment to an email message or a link to its file on a network resource (e.g. a URL to an infected file on a compromised website or a hacker-owned website). In the first case, the worm code activates when the infected attachment is opened (launched). In the second case, the code is activated when the link to the infected file is opened. In both case, the result is the same: the worm code is activated. Email-Worms use a range of methods to send infected emails. The most common are: using a direct connection to a SMTP server using the email directory built into the worm’s code using MS Outlook services using Windows MAPI functions. Email-Worms use a number of different sources to find email addresses to which infected emails will be sent: the address book in MS Outlook a WAB address database .txt files stored on the hard drive: the worm can identify which strings in text files are email addresses emails in the inbox (some Email-Worms even “reply” to emails found in the inbox) Many Email-Worms use more than one of the sources listed above. There are also other sources of email addresses, such as address books associated with web-based email services.Read more
Platform: Win32
Win32 is an API on Windows NT-based operating systems (Windows XP, Windows 7, etc.) that supports execution of 32-bit applications. One of the most widespread programming platforms in the world.Description
Technical Details
Swen is a very dangerous worm-virus that spreads across the Internet via email (in the form of an infected file attachment), the Kazaa file sharing network, IRC channels, and open network resources.
Swen is written in Microsoft Visual C++ and is 105KB (106496 Bytes) in size.
The worm activates when a victim launches the infected file (double clicking on the file attachment) or when a victim machine's email application is vulnerable to the IFrame.FileDownload vulnerability (also exploited by the Internet worms Klez and Tanatos). Once run, Swen installs itself in the system and begins its propogation routine.
You can download the patch released in March 2001 for the IFrame vulnerability: Microsoft Security Bulletin MS01-20.
The worm blocks many anti-virus programs and firewalls. Its algorithm and parts of the code text are almost identical to that of another Internet worm called I-Worm.Gibe, although the programming language used is different.
Installation
When first launched, the worm may display the "Microsoft Internet Update Pack" message box. Then it imitates patch installation:
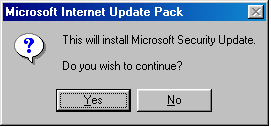
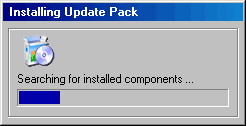
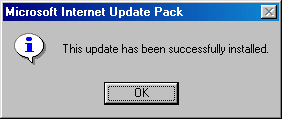
The worm then copies itself under one of the names below into the Windows directory. The name may consist of several parts.
First possibility:
- Kazaa Lite
KaZaA media desktop
KaZaA
WinRar
WinZip
Winamp
Mirc
Download Accelerator
GetRight FTP
Windows Media Player
- Key generator
Hack
Hacked
Warez
Upload
Installer
Upload
Installer
Second possibility:
- Bugbear
Yaha
Gibe
Sircam
Sobig
Klez - Remover
RemovalTool
Cleaner
Fixtool
Third possibility:
Aol Hacker
Yahoo Hacker
Hotmail Hacker
10.000 Serials
Jenna Jameson
Hardporn
Sex
Xbox Emulator
Emulator Ps2
Xp Update
Xxx Video
Sick Joke
Xxx Pictures
My Naked Sister
Hallucinogenic Screensaver
Cooking With Cannabis
Magic Mushrooms Growing
Virus Generator
The new file is registered in the Windows system registry auto-run key:
HKLMSoftwareMicrosoftWindowsCurrentVersionRun random sequence= %windir%file name autorun
An identification key is created, which contains the worms' configuration settings:
HKLMSoftwareMicrosoftWindowsCurrentVersionExplorer random sequence
The worm then creates a file named after the infected host machine with a BAT extension in the Windows folder. The file contains following the commands:
@ECHO OFF
IF NOT "%1"=="".exe %1
Then the worm changes the key values in HKLMSoftwareClasses in such a way so as to hook onto execution every time the BAT, COM, EXE, PIF, REG and SCR file types are launched.
HKCRbatfileshellopencommand Default = %windir%"%1" %* HKCRcomfileshellopencommand Default = %windir% "%1" %* HKEY_CLASSES_ROOTexefileshellopencommand Default = %windir% "%1" %* HKCRpiffileshellopencommand Default = %windir% "%1" %* HKCRregfileshellopencommand Default = %windir% showerror HKCRscrfileshellconfigcommand Default = %windir% "%1" HKCRscrfileshellopencommand Default = %windir% "%1" /S
Disables user capability to edit the system registry:
HKCU.DEFAULTSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem DisableRegistryTools = 01 00 00 00
When first launched, the worm accesses the following remote website:
http://ww2.fce.vutbr.cz/bin/counter.gif/link=bacillus&width=6&set=cnt006
This counter indicates the number of infected computers.
When attempting to execute a new copy of the worm on the already infected machine the worm displays the following message:
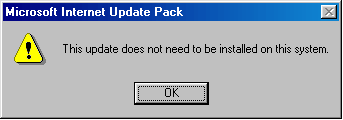
The worm scans all disks for files with extensions DBX, MDX, EML, WAB and also that contain either HT or ASP in the extension. Swem then extracts any email addresses that it can find and saves them in a file named germs0.dbv.
The worm attempts to connect to one of 350 servers identified in the file swen1.dat, in order to send infected emails. If connection is impossible the worm then displays the following error message about a MAPI 32 Exception:
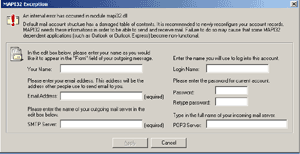
and requests a correct email address, as well as a correct SMTP server.
Propagation via Email
The worm mails itself to all available addresses using a direct connection to an SMTP server. The infected emails are in HTML format and contain an attachment (the actual worm).

Sender name (consists of several parts):
- Microsoft
MS
- (may not be used)
Corporation
- (may not be used)
Program
Internet
Network
- (always included with part 3)
Security
- (may not be used)
Division
Section
Department
Center
- (may not be used)
Public
Technical
Customer
- (may not be used)
Bulletin
Services
Assistance
Support
For example:
Microsoft Internet Security Section
MS Technical Assistance
Sender address (consists of 2 parts):
- before "@": random sequence (example: tuevprkpevcg-gxwi@, dwffa@);
- after "@": consists of 2 parts (though only one may be used):
- news
newsletter
bulletin
confidence
advisor
updates
technet
support
- msdn
microsoft
ms
msn
For example: "newsletter.microsoft" or simply "support". If two parts are used, then they are separated by ".", or "_".
After the "." the domain is either "com" or "net".
- news
Subject (consists of various parts):
- Latest
New
Last
Newest
Current
- Net
Network
Microsoft
Internet
- Security
Critical
- Upgrade
Pack
Update
Patch
Body:
MS Client (Consumer,Partner,User - chosen at random)
this is the latest version of security update, the
"September 2003, Cumulative Patch" update which resolves
all known security vulnerabilities affecting
MS Internet Explorer, MS Outlook and MS Outlook Express.
Install now to protect your computer
from these vulnerabilities, the most serious of which could
allow an attacker to run code on your system.
This update includes the functionality =
of all previously released patches.
System requirements: Windows 95/98/Me/2000/NT/XP
This update applies to:
- MS Internet Explorer, version 4.01 and later
- MS Outlook, version 8.00 and later
- MS Outlook Express, version 4.01 and later
Recommendation: Customers should install the patch =
at the earliest opportunity.
How to install: Run attached file. Choose Yes on displayed dialog box.
How to use: You don't need to do anything after installing this item.
Signature:
Microsoft Product Support Services and Knowledge Base articles =
can be found on the Microsoft Technical Support web site.
http://support.microsoft.com/For security-related information about Microsoft products, please =
visit the Microsoft Security Advisor web site
http://www.microsoft.com/security/Thank you for using Microsoft products.
Please do not reply to this message.
It was sent from an unmonitored e-mail address and we are unable =
to respond to any replies.----------------------------------------------
The names of the actual companies and products mentioned =
herein are the trademarks of their respective owners.
Attachment name:
patch[random number].exe
install[random number].exe
q[random number].exe
update[random number].exe
The actual content of the body may be less complicated, depending on various circumstances.
- The Subject may contain:
Letter
Advise
Message
Announcement
Report
Notice
Bug
Error
Abort
Failed
User Unknown - The body may contain:
Hi!
This is the qmail program
Message from [random value]
I'm sorry
I'm sorry to have to inform that
I'm afraid
I'm afraid I wasn't able to deliver your message to the following addresses
the message returned below could not be delivered
I wasn't able to deliver your message
to one or more destinations
In some cases the worm may send copies of itself in archived form - ZIP or RAR.
Propagation via Kazaa
Swen propagates via the Kazaa file-sharing network by copying itself under random names in the file exchange directory in Kazaa Lite. It also creates a subdirectory in the Windows Temp folder with random names making several copies of itself with random names as well.
This folder is identified in the Windows system registry as Local Content for Kazaa file-sharing system.
HKCUSoftwareKazaaLocalContent dir99 = 012345:%Windir%%temp%folder name
As a result, the new files created by Swen become available to other Kazaa network users.
Propagation via IRC channels
The worm scans for installed mIRC client. If it's detected Swen then modifies the script.ini file by adding its propagation procedures. Whereupon the scrip.ini file sends the infected file from the Windows directory to all users that connect to the now-infected IRC channel.
Propagation via LAN
The worm scans all available drives. If it finds a network drive it copies itself there in the following folders under a random name:
windowsall usersstart menuprogramsstartup
windowsstart menuprogramsstartup
winmeall usersstart menuprogramsstartup
winmestart menuprogramsstartup
win95all usersstart menuprogramsstartup
win95start menuprogramsstartup
win98all usersstart menuprogramsstartup
win98start menuprogramsstartup
document and settingsall usersstart menuprogramsstartup
document and settingsdefault userstart menuprogramsstartup
document and settingsadministratorstart menuprogramsstartup
winntprofilesall usersstart menuprogramsstartup
winntprofilesdefault userstart menuprogramsstartup
winntprofilesadministratorstart menuprogramsstartup
Other
The worm attempts to block the launch and work of various anti-virus software and firewalls:
_avp ackwin32 anti-trojan aplica32 apvxdwin autodown avconsol ave32 avgcc32 avgctrl avgw avkserv avnt avp avsched32 avwin95 avwupd32 blackd blackice bootwarn ccapp ccshtdwn cfiadmin cfiaudit cfind cfinet claw95 dv95 ecengine efinet32 esafe espwatch f-agnt95 findviru fprot f-prot fprot95 f-prot95 fp-win frw f-stopw gibe iamapp iamserv ibmasn ibmavsp icload95 icloadnt icmon icmoon icssuppnt icsupp iface iomon98 jedi
kpfw32 lockdown2000 lookout luall moolive mpftray msconfig nai_vs_stat navapw32 navlu32 navnt navsched navw nisum nmain normist nupdate nupgrade nvc95 outpost padmin pavcl pavsched pavw pcciomon pccmain pccwin98 pcfwallicon persfw pop3trap pview rav regedit rescue safeweb serv95 sphinx sweep tca tds2 vcleaner vcontrol vet32 vet95 vet98 vettray vscan vsecomr vshwin32 vsstat webtrap wfindv32 zapro zonealarm
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com