Parent class: VirWare
Viruses and worms are malicious programs that self-replicate on computers or via computer networks without the user being aware; each subsequent copy of such malicious programs is also able to self-replicate. Malicious programs which spread via networks or infect remote machines when commanded to do so by the “owner” (e.g. Backdoors) or programs that create multiple copies that are unable to self-replicate are not part of the Viruses and Worms subclass. The main characteristic used to determine whether or not a program is classified as a separate behaviour within the Viruses and Worms subclass is how the program propagates (i.e. how the malicious program spreads copies of itself via local or network resources.) Most known worms are spread as files sent as email attachments, via a link to a web or FTP resource, via a link sent in an ICQ or IRC message, via P2P file sharing networks etc. Some worms spread as network packets; these directly penetrate the computer memory, and the worm code is then activated. Worms use the following techniques to penetrate remote computers and launch copies of themselves: social engineering (for example, an email message suggesting the user opens an attached file), exploiting network configuration errors (such as copying to a fully accessible disk), and exploiting loopholes in operating system and application security. Viruses can be divided in accordance with the method used to infect a computer:- file viruses
- boot sector viruses
- macro viruses
- script viruses
Class: Email-Worm
Email-Worms spread via email. The worm sends a copy of itself as an attachment to an email message or a link to its file on a network resource (e.g. a URL to an infected file on a compromised website or a hacker-owned website). In the first case, the worm code activates when the infected attachment is opened (launched). In the second case, the code is activated when the link to the infected file is opened. In both case, the result is the same: the worm code is activated. Email-Worms use a range of methods to send infected emails. The most common are: using a direct connection to a SMTP server using the email directory built into the worm’s code using MS Outlook services using Windows MAPI functions. Email-Worms use a number of different sources to find email addresses to which infected emails will be sent: the address book in MS Outlook a WAB address database .txt files stored on the hard drive: the worm can identify which strings in text files are email addresses emails in the inbox (some Email-Worms even “reply” to emails found in the inbox) Many Email-Worms use more than one of the sources listed above. There are also other sources of email addresses, such as address books associated with web-based email services.Read more
Platform: VBS
Visual Basic Scripting Edition (VBScript) is a scripting language interpreted by Windows Script Host. VBScript is widely used to create scripts on Microsoft Windows operating systems.Description
Technical Details
This is an extremely dangerous variant of the "LoveLetter" Internet worm. Just as with its forerunner "LoveLetter", the "NewLove" worm is written in Visual Basic Script language and spreads as a VBS file with a random name. The worm installs itself into the system, gains access to the MS Outlook address book, and sends itself to all addresses listed in there.
The infected message subject begins with "FW:" and is completed with a random text up to 30 characters in length and random extension from the following list:
Doc, Xls, Mdb, Bmp, Mp3, Txt, Jpg, Gif, Mov, Url, Htm, Txt
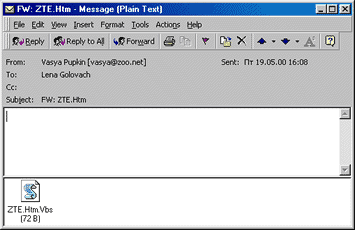
This also serves as the name of the attached file, for example:
FW: VPAVQXCUUNGUFLTJSLNAUTQZXJUG.Bmp
FW: QKUPLSXOOIBPAGNENGIVPN.Mp3
FW: TNXSOVARRLESDJQHQJLYSQNWV.Mdb
FW: HBLHCJOFFZS.Mdb
FW: MGQMHOTKKEXLWCJAJ.Doc
FW: SMXSNUZRRKDRCJQGPIKXRQNWU.Mdb
FW: CWGCXE.Mp3
The message body is empty, and there is a VBS file attached with the same file name that is in the subject line, but with an added ".VBS" extension. Depending on the system settings, a real extension of the attached file (".vbs") may not be shown. In this case, the filename of an attached file is displayed as shown above (with no "FW:").
When the attached file is activated (by double clicking, for example), the worm sends its copies to all addresses from the MS Outlook address base.
The worm then destroys the computer. It scans all local and mapped disk drives and replaces all files with its copy, and adds the ".VBS" extension to file names (for example COMMAND.COM becomes COMMAND.COM.VBS). As a result, all files on all accessable drives are totally destroyed.
Because of this, the worm is able to spread just once - it sends its copy to all availabe addresses and then destroys the computer.
The worm is able to spread only in the instance that MS Outlook is installed in the system. The worm payload routine is activated independent of the e-mail system installed on the computer. In the case that there is another e-mail system installed, the worm does not send infected e-mails, instead destroying all files on the computer.
The worm is polymorphic. Upon each infection, it inserts random comments into its code. The worm does this each time it spreads, and as a result, its size grows depending on its generation (about 60% of the current size), for example:
1st generation: 110Kb
2st generation: 248Kb
3st generation: 403Kb
4st generation: 585Kb
5st generation: 805Kb
6st generation: 1040Kb
e.t.c.
The "pure" worm code is just about 5Kb in size.
Protection for this type of worms has already been released by Kaspersky. The "AVP Script Checker" protects the system against the new worm and prevents infection. We strongly recommend you download "AVP Script Checker" from our Kasperky Lab Web sites.
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com