Parent class: VirWare
Viruses and worms are malicious programs that self-replicate on computers or via computer networks without the user being aware; each subsequent copy of such malicious programs is also able to self-replicate. Malicious programs which spread via networks or infect remote machines when commanded to do so by the “owner” (e.g. Backdoors) or programs that create multiple copies that are unable to self-replicate are not part of the Viruses and Worms subclass. The main characteristic used to determine whether or not a program is classified as a separate behaviour within the Viruses and Worms subclass is how the program propagates (i.e. how the malicious program spreads copies of itself via local or network resources.) Most known worms are spread as files sent as email attachments, via a link to a web or FTP resource, via a link sent in an ICQ or IRC message, via P2P file sharing networks etc. Some worms spread as network packets; these directly penetrate the computer memory, and the worm code is then activated. Worms use the following techniques to penetrate remote computers and launch copies of themselves: social engineering (for example, an email message suggesting the user opens an attached file), exploiting network configuration errors (such as copying to a fully accessible disk), and exploiting loopholes in operating system and application security. Viruses can be divided in accordance with the method used to infect a computer:- file viruses
- boot sector viruses
- macro viruses
- script viruses
Class: Email-Worm
Email-Worms spread via email. The worm sends a copy of itself as an attachment to an email message or a link to its file on a network resource (e.g. a URL to an infected file on a compromised website or a hacker-owned website). In the first case, the worm code activates when the infected attachment is opened (launched). In the second case, the code is activated when the link to the infected file is opened. In both case, the result is the same: the worm code is activated. Email-Worms use a range of methods to send infected emails. The most common are: using a direct connection to a SMTP server using the email directory built into the worm’s code using MS Outlook services using Windows MAPI functions. Email-Worms use a number of different sources to find email addresses to which infected emails will be sent: the address book in MS Outlook a WAB address database .txt files stored on the hard drive: the worm can identify which strings in text files are email addresses emails in the inbox (some Email-Worms even “reply” to emails found in the inbox) Many Email-Worms use more than one of the sources listed above. There are also other sources of email addresses, such as address books associated with web-based email services.Read more
Platform: Win32
Win32 is an API on Windows NT-based operating systems (Windows XP, Windows 7, etc.) that supports execution of 32-bit applications. One of the most widespread programming platforms in the world.Description
Technical Details
Melare is a worm virus spreading via the Internet as an e-mail attachment. The worm itself is a Windows PE EXE file about 6KB in length when compressed by UPX, the decompressed size is about 15KB. It is written in Visual Basic.The worm activates from infected email only if a user clicks on the attached file. Note that the real attached .EXE file name is hidden by a false .JPG name. As a result the infected .EXE file is displayed as a .JPG image file (picture), though upon opening this attachment it is executed as true EXE file. When launched from MS Outlook 97 SP2 such attached files are blocked (in the default mode).
The worm then installs itself into the system, runs its spreading routine and payload.
Installation
While installing the worm copies itself to the Windows directory under the name csrss.EXE and registers this file in the system registry auto-run key:
HKLMSoftwareMicrosoftWindowsCurrentVersionRun SystemSARS32 = %WindowsDir%csrss.EXE
Spreading
To send infected messages the worm uses MS Outlook and sends messages to all the addresses found in the Outlook address book.
Infected messages have the following attributes:
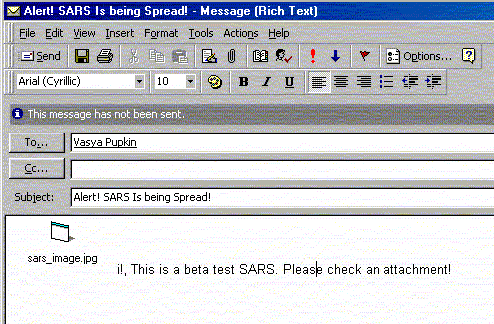
The beginning of the message body text may be covered by a "JPG attach" icon.
Payload
On the 1st, 4th, 8th, 12th, 16th, 20th, 24th and 28th of each month the worm deletes all *.DLL, *.NLS, *.OCX files in the current directory (in most cases this would be the Windows directory).
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com