Parent class: VirWare
Viruses and worms are malicious programs that self-replicate on computers or via computer networks without the user being aware; each subsequent copy of such malicious programs is also able to self-replicate. Malicious programs which spread via networks or infect remote machines when commanded to do so by the “owner” (e.g. Backdoors) or programs that create multiple copies that are unable to self-replicate are not part of the Viruses and Worms subclass. The main characteristic used to determine whether or not a program is classified as a separate behaviour within the Viruses and Worms subclass is how the program propagates (i.e. how the malicious program spreads copies of itself via local or network resources.) Most known worms are spread as files sent as email attachments, via a link to a web or FTP resource, via a link sent in an ICQ or IRC message, via P2P file sharing networks etc. Some worms spread as network packets; these directly penetrate the computer memory, and the worm code is then activated. Worms use the following techniques to penetrate remote computers and launch copies of themselves: social engineering (for example, an email message suggesting the user opens an attached file), exploiting network configuration errors (such as copying to a fully accessible disk), and exploiting loopholes in operating system and application security. Viruses can be divided in accordance with the method used to infect a computer:- file viruses
- boot sector viruses
- macro viruses
- script viruses
Class: Email-Worm
Email-Worms spread via email. The worm sends a copy of itself as an attachment to an email message or a link to its file on a network resource (e.g. a URL to an infected file on a compromised website or a hacker-owned website). In the first case, the worm code activates when the infected attachment is opened (launched). In the second case, the code is activated when the link to the infected file is opened. In both case, the result is the same: the worm code is activated. Email-Worms use a range of methods to send infected emails. The most common are: using a direct connection to a SMTP server using the email directory built into the worm’s code using MS Outlook services using Windows MAPI functions. Email-Worms use a number of different sources to find email addresses to which infected emails will be sent: the address book in MS Outlook a WAB address database .txt files stored on the hard drive: the worm can identify which strings in text files are email addresses emails in the inbox (some Email-Worms even “reply” to emails found in the inbox) Many Email-Worms use more than one of the sources listed above. There are also other sources of email addresses, such as address books associated with web-based email services.Read more
Platform: Win32
Win32 is an API on Windows NT-based operating systems (Windows XP, Windows 7, etc.) that supports execution of 32-bit applications. One of the most widespread programming platforms in the world.Description
Technical Details
I-Worm.Masana is a worm virus spreading via the Internet as an attachment to infected emails. The worm itself is a Windows PE EXE file about 107Kb in size - ASPack compresses it, the decompressed size is about 138Kb, written in Delphi.
Infected messages contain the following:
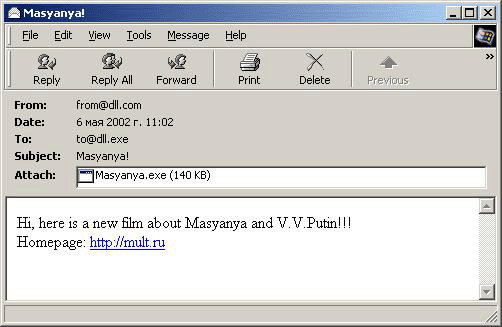
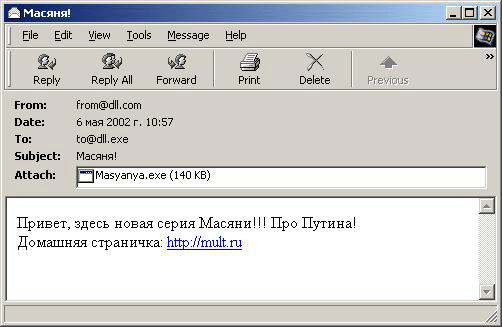
Another variant is the same subject and body as above but in Russian.
The worm activates from infected email only when a user clicks on the attached file. The worm then installs itself into the system, runs its spreading routine and payload.
The worm has bugs in its code; as a result some of its routines don't work.
Installing
While installing the worm copies itself into the Windows system directory with under the msys32.exe name and registers this file in the system registry (under Windows NT) or in the SYSTEM.INI (under Windows 9x) auto-run keys:
SYSTEM.INI
[boot]
shell=Explorer.exe msys32.exe -dontrunold
HKLMSoftwareMicrosoftWindowsCurrentVersionRun
Run as Administrator
Under Windows NT systems the worm gains Admin privileges. To do this the worm uses a breach in Windows NT security (so-called DepPloit exploit).
The Masana worm creates two additional files on disk that manage the exploit:
ERunAsX.exeThe worm then creates another copy of itself under the name EEXPLORER.EXE name and by using DepPLoit exploit starts this copy with administrator rights.
ERunAsX.dll
Spreading
To send infected messages the worm uses Windows MAPI functions.
To get victim email addresses Masana:
- looks for *.HTM* files and extracts email-like strings
- by using Windows MAPI functions it reads all unread messages from the Inbox and answers them.
Each time Masana is run it also sends infected message to the masyana@nm.ru address. This message looks as follows:
Subject: Masyanya!Payload
Body: gygygy!
Attach: Masyanya.exe
On Mondays the worm starts a DoS (Denial of Service) attack on kavkaz.org.
Other
This worm also:
- disables the MS Outlook Express 5.0 MAPISendMail warning.
- adds to the system the user named masyanechkaa with Admin privileges (under Windows NT)
I-Worm.Masana also contains the text string:
I-Worm.Masyanya v1.0 8) Just a hello-world worm...
The worm also creates an additional registry key that indicates the system is already infected:
HKCUEnvironment
ID = 1
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com
Found an inaccuracy in the description of this vulnerability? Let us know!