Parent class: Pornware
Pornware is the term used for programs that display pornographic material to the user. Programs in the Pornware class may be deliberately installed by the user in order to search for and obtain pornographic material. In such cases, the programs are not unwanted. On the other hand, the very same programs can be installed on a user’s computer by malicious users by exploiting operating system or browser vulnerabilities, or by using Trojans such as Trojan-Downloader and Trojan-Dropper. This is usually done to push advertisements for fee-based pornographic websites and services that a typical user might otherwise not be aware of.Read more
Class: Porn-Downloader
This behaviour downloads pornographic media files to the user’s computer from the Internet. Unlike malicious programs, such programs notify the user of their actions.Read more
Platform: Win32
Win32 is an API on Windows NT-based operating systems (Windows XP, Windows 7, etc.) that supports execution of 32-bit applications. One of the most widespread programming platforms in the world.Description
Technical Details
This is an Internet worm spreading via e-mail attached as an EXE file. The worm itself is a Win32 executable file about 30Kb in length, written in Visual Basic.
The worm seems to be based on the "Melissa" macro-virus worm - the functions and sequence of instructions in the worm code are very similar to the "Melissa" source code. It seems that this worm was compiled from a slightly modified "Melissa" source.
When the worm EXE file is being run from an attachment, it sends infected messages and registers itself in a system to run each time Windows starts up.
To spread from an infected computer, the worm uses MS Outlook by obtaining addresses from the MS Outlook Address Book and sends messages there.
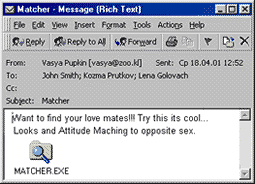
The message Subject, Body and Attachment appear follows:
Subject: Matcher
Body: Want to find your love mates!!! Try this its cool... Looks and Attitude Maching to opposite sex.
Attach: matcher.exe
To install into a system, the worm copies itself to the Windows system directory with the MATCHER.EXE name, and registers this file in the Windows registry auto-run section:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
%SystemDir%matcher.exe
where %SystemDir% is the name of the Windows system directory.
The worm also adds to the end of C:AUTOEXEC.BAT the commands:
@echo off
echo from: Bugger
pause
These commands display the "from: Bugger" message when system is booting up and processes the AUTOEXEC.BAT.
Read more
Find out the statistics of the vulnerabilities spreading in your region on statistics.securelist.com